workday segregation of duties matrix
 To do this, you need to determine which business roles need to be combined into one user account. Our community of professionals is committed to lifetime learning, career progression and sharing expertise for the benefit of individuals and organizations around the globe. 21 Vanamali, S.; Role Engineering: The Cornerstone of RBAC, ISACA Journal, vol. Copyright 2023 Pathlock. No organization is able to entirely restrict sensitive access and eliminate SoD risks. Eight roles were addressed in the development of the UCB separation-of-duties rules. 2017
Similarly, the person in charge of payments performs some checks before fulfilling the payment request. If your organization is regularly audited by third parties, they will appreciate the rigor and the archived results of the audits run with Genie. 3: Understand and Prioritize the Risks. Securing the Workday environment is an endeavor that will require each organization to balance the principle of least privileged access with optimal usability, administrative burden and agility to respond to business changes. If any conflicts are left, some compensating control must be put in place to properly manage the associated risk. ISACA delivers expert-designed in-person training on-site through hands-on, Training Week courses across North America, through workshops and sessions at conferences around the globe, and online. BOR Payroll Data Reconcile the transaction. We have developed a variety of tools and accelerators, based on Workday security and controls experience, that help optimize what you do every day. In the literature about SoD, there is not much discussion about scoping SoD requirements. Remember our goal is to ensure, nosingle personis responsible for every stage in a process. In this case, conflicts are introduced while designing processes, procedures and roles. This can go a long way to mitigate risks and reduce the ongoing effort required to maintain a stable and secure Workday environment. Applying scoping rules to demarcate the playing field can provide numerous advantages during the implementation phase. Understand the difference Generally, conventions help system administrators and support partners classify and intuitively understand the general function of the security group. Meet some of the members around the world who make ISACA, well, ISACA. With time, conflicts can be unintentionally introduced, allowing controls to be circumvented if careful consideration is not given to each configuration change. WebBOR_SEGREGATION_DUTIES. Technology Consulting - Enterprise Application Solutions. Websegregation of payroll duties with the aim of minimizing errors and preventing fraud involving the processing and distribution of payroll. Websegregation of duties relies on a transparent, role-based access right structure developed on the basis of business processes; our Identity and Access Management Services help A visual depiction of processes can be used as the basis to build a matrix of activities, which are then checked for incompatibilities.19 Those who evaluate SoD on processes written at this high level of detail should consider doing the following: The first choice has the advantage in that it reduces the size of the matrices. In enterprises, process activities are often described by means of some procedure or in a diagram in some standard notation, such as a business process model and notation. Regardless of the school of thought adopted for Workday security architecture, applying the principles discussed in this post will help to design and rollout Workday security effectively. This is a segregation (or separation) of duties. The figure below depicts a small piece of an SoD matrix, which shows four main purchasing roles. The 100 most critical and common segregation of duties. WebSegregation of duties matrix DataConsulting SAP Security Concepts Segregation of Duties Sensitive October 7th, 2018 - place on reports coming from SAP ? For example, a table defining organizational structure can have four columns defining: After setting up your organizational structure in the ERP system, you need to create an SoD matrix. Often includes access to enter/initiate more sensitive transactions. Information and technology power todays advances, and ISACA empowers IS/IT professionals and enterprises. Alter the process description by grouping or removing activities in order to hide details that are not relevant to SoD. With over 30 years of digital design, development, and delivery under our belts, if youve got a digital challenge, well work with you to get game-changing results. Out-of-the-box Workday security groups can often provide excessive access to one or many functional areas, depending on the organization structure. Failure to consider these nuances will create high volumes of noise during theanalysis phase via false positives. ISACA resources are curated, written and reviewed by expertsmost often, our members and ISACA certification holders. Duties can be seen, then, as properly separated if there is a set of controls on each process so that the risk is properly mitigated (e.g., authorizations are independently verified and reconciled and reports are independently checked against accounts receivable). You can explore these considerations and more in our latest Whitepaper.
To do this, you need to determine which business roles need to be combined into one user account. Our community of professionals is committed to lifetime learning, career progression and sharing expertise for the benefit of individuals and organizations around the globe. 21 Vanamali, S.; Role Engineering: The Cornerstone of RBAC, ISACA Journal, vol. Copyright 2023 Pathlock. No organization is able to entirely restrict sensitive access and eliminate SoD risks. Eight roles were addressed in the development of the UCB separation-of-duties rules. 2017
Similarly, the person in charge of payments performs some checks before fulfilling the payment request. If your organization is regularly audited by third parties, they will appreciate the rigor and the archived results of the audits run with Genie. 3: Understand and Prioritize the Risks. Securing the Workday environment is an endeavor that will require each organization to balance the principle of least privileged access with optimal usability, administrative burden and agility to respond to business changes. If any conflicts are left, some compensating control must be put in place to properly manage the associated risk. ISACA delivers expert-designed in-person training on-site through hands-on, Training Week courses across North America, through workshops and sessions at conferences around the globe, and online. BOR Payroll Data Reconcile the transaction. We have developed a variety of tools and accelerators, based on Workday security and controls experience, that help optimize what you do every day. In the literature about SoD, there is not much discussion about scoping SoD requirements. Remember our goal is to ensure, nosingle personis responsible for every stage in a process. In this case, conflicts are introduced while designing processes, procedures and roles. This can go a long way to mitigate risks and reduce the ongoing effort required to maintain a stable and secure Workday environment. Applying scoping rules to demarcate the playing field can provide numerous advantages during the implementation phase. Understand the difference Generally, conventions help system administrators and support partners classify and intuitively understand the general function of the security group. Meet some of the members around the world who make ISACA, well, ISACA. With time, conflicts can be unintentionally introduced, allowing controls to be circumvented if careful consideration is not given to each configuration change. WebBOR_SEGREGATION_DUTIES. Technology Consulting - Enterprise Application Solutions. Websegregation of payroll duties with the aim of minimizing errors and preventing fraud involving the processing and distribution of payroll. Websegregation of duties relies on a transparent, role-based access right structure developed on the basis of business processes; our Identity and Access Management Services help A visual depiction of processes can be used as the basis to build a matrix of activities, which are then checked for incompatibilities.19 Those who evaluate SoD on processes written at this high level of detail should consider doing the following: The first choice has the advantage in that it reduces the size of the matrices. In enterprises, process activities are often described by means of some procedure or in a diagram in some standard notation, such as a business process model and notation. Regardless of the school of thought adopted for Workday security architecture, applying the principles discussed in this post will help to design and rollout Workday security effectively. This is a segregation (or separation) of duties. The figure below depicts a small piece of an SoD matrix, which shows four main purchasing roles. The 100 most critical and common segregation of duties. WebSegregation of duties matrix DataConsulting SAP Security Concepts Segregation of Duties Sensitive October 7th, 2018 - place on reports coming from SAP ? For example, a table defining organizational structure can have four columns defining: After setting up your organizational structure in the ERP system, you need to create an SoD matrix. Often includes access to enter/initiate more sensitive transactions. Information and technology power todays advances, and ISACA empowers IS/IT professionals and enterprises. Alter the process description by grouping or removing activities in order to hide details that are not relevant to SoD. With over 30 years of digital design, development, and delivery under our belts, if youve got a digital challenge, well work with you to get game-changing results. Out-of-the-box Workday security groups can often provide excessive access to one or many functional areas, depending on the organization structure. Failure to consider these nuances will create high volumes of noise during theanalysis phase via false positives. ISACA resources are curated, written and reviewed by expertsmost often, our members and ISACA certification holders. Duties can be seen, then, as properly separated if there is a set of controls on each process so that the risk is properly mitigated (e.g., authorizations are independently verified and reconciled and reports are independently checked against accounts receivable). You can explore these considerations and more in our latest Whitepaper.  Governance is not included in figure 2 since risk factors due to lack of governance are less specific and more difficult to match with single duties (nonetheless, they may have high impacts on businesses). As Workday supports business transactions and stores critical business data, it is crucial for organisations to clearly define where material fraud risks could impact financial reporting processes. If a worker can proxy in as another worker who for instance can add security groups than they could proxy in and add additional security to themselves which might violate your Segregation of Duties policy. Create a spreadsheet with IDs of assignments in the X axis, and the same IDs along the Y axis. WebWhether a company is just considering a Workday implementation, or is already operational and looking for continuous improvement, an evaluation of internal controls will enable In high risk areas, such access should be actively monitored to reduce the risk of fraudulent, malicious intent. This layout can help you easily find an overlap of duties that might create risks. It is important to have a well-designed and strong security architecture within Workday to ensure smooth business operations, minimize risks, meet regulatory requirements, and improve an organizations governance, risk and compliance (GRC) processes. Recording payments from clients or vendors. This Query is being developed to help assess potential segregation of duties issues. Both of these methods were tested, and it was found that the first one was more effective. The SoD implementation tested for this article listed more than 80 potential SoD conflicts, along with the compensating controls that had been applied to reduce risk to acceptable levels. Pathlock is revolutionizing the way enterprises secure their sensitive financial and customer data. 1. Get the SOD Matrix.xlsx you need. With Workday at the heart of your organisation, establishing foundational IT General controls, including appropriate SoD, is a critical internal control consideration relevant to SOX compliance efforts. I hope this helps but feel free to follow up. There are no individuals performing two different duties; there are two individuals performing the same duty (a custody duty). Whether you are in or looking to land an entry-level position, an experienced IT practitioner or manager, or at the top of your field, ISACA offers the credentials to prove you have what it takes to excel in your current and future roles. For example, two employees may be in charge of recording and authorizing transactions on the same set of assets, provided that, for every single asset, one employee records the transactions data and the other employee authorizes the operation. SoD matrices can help keep track of a large number of different transactional duties. Conflicts originate from the attribution of conflicting duties to the same actor. 27 Using 24 Colantonio, A.; Role Mining Techniques To Improve RBAC Administration, Rome, Italy, 2011 SOD ToolsExample Control Objectives (Summarized) IdM technique could be deployed to address some of the objective IdM technique could be deployed to address most of the objective. This fourth duty encompasses operations that verify and review the correctness of operations made by other individuals, whether they are custody, recording or authorization operations.5 Some of the core SoD elements are actors, duties, risk, scope, activities, roles, systems and applications, and user profiles. 7 ISACA, COBIT 5: Enabling Processes, USA, 2012 Given the size and complexity of most organizations, effectively managing user access to Workday can be challenging. We are all of you! Defining adequate security policies and requirements will enable a clean security role design with few or no unmitigated risks of which the organization is not aware. (Such profiles are called Yes/No profiles, meaning that a user is either authorized or not authorized to access an application.). In this case, if assets are, for instance, accounts receivable, two employees can both record the account receivable data and authorize transactions.
Governance is not included in figure 2 since risk factors due to lack of governance are less specific and more difficult to match with single duties (nonetheless, they may have high impacts on businesses). As Workday supports business transactions and stores critical business data, it is crucial for organisations to clearly define where material fraud risks could impact financial reporting processes. If a worker can proxy in as another worker who for instance can add security groups than they could proxy in and add additional security to themselves which might violate your Segregation of Duties policy. Create a spreadsheet with IDs of assignments in the X axis, and the same IDs along the Y axis. WebWhether a company is just considering a Workday implementation, or is already operational and looking for continuous improvement, an evaluation of internal controls will enable In high risk areas, such access should be actively monitored to reduce the risk of fraudulent, malicious intent. This layout can help you easily find an overlap of duties that might create risks. It is important to have a well-designed and strong security architecture within Workday to ensure smooth business operations, minimize risks, meet regulatory requirements, and improve an organizations governance, risk and compliance (GRC) processes. Recording payments from clients or vendors. This Query is being developed to help assess potential segregation of duties issues. Both of these methods were tested, and it was found that the first one was more effective. The SoD implementation tested for this article listed more than 80 potential SoD conflicts, along with the compensating controls that had been applied to reduce risk to acceptable levels. Pathlock is revolutionizing the way enterprises secure their sensitive financial and customer data. 1. Get the SOD Matrix.xlsx you need. With Workday at the heart of your organisation, establishing foundational IT General controls, including appropriate SoD, is a critical internal control consideration relevant to SOX compliance efforts. I hope this helps but feel free to follow up. There are no individuals performing two different duties; there are two individuals performing the same duty (a custody duty). Whether you are in or looking to land an entry-level position, an experienced IT practitioner or manager, or at the top of your field, ISACA offers the credentials to prove you have what it takes to excel in your current and future roles. For example, two employees may be in charge of recording and authorizing transactions on the same set of assets, provided that, for every single asset, one employee records the transactions data and the other employee authorizes the operation. SoD matrices can help keep track of a large number of different transactional duties. Conflicts originate from the attribution of conflicting duties to the same actor. 27 Using 24 Colantonio, A.; Role Mining Techniques To Improve RBAC Administration, Rome, Italy, 2011 SOD ToolsExample Control Objectives (Summarized) IdM technique could be deployed to address some of the objective IdM technique could be deployed to address most of the objective. This fourth duty encompasses operations that verify and review the correctness of operations made by other individuals, whether they are custody, recording or authorization operations.5 Some of the core SoD elements are actors, duties, risk, scope, activities, roles, systems and applications, and user profiles. 7 ISACA, COBIT 5: Enabling Processes, USA, 2012 Given the size and complexity of most organizations, effectively managing user access to Workday can be challenging. We are all of you! Defining adequate security policies and requirements will enable a clean security role design with few or no unmitigated risks of which the organization is not aware. (Such profiles are called Yes/No profiles, meaning that a user is either authorized or not authorized to access an application.). In this case, if assets are, for instance, accounts receivable, two employees can both record the account receivable data and authorize transactions.  In an enterprise, process activities are usually represented by diagrams or flowcharts, with a level of detail that does not directly match tasks performed by employees. Segregation of Duties: To define a Segregation of Duties matrix for the organisation, identify and manage violations. Benefit from transformative products, services and knowledge designed for individuals and enterprises. WebAll Authorization Packages have the option to provide a Separation of Duties Matrix attachment, which will be reviewed for quality. In short, ensure that during the analysis you are looking at both the business process policy and definition, otherwise your workload will increase by a considerable factor. Segregation of duties is the principle that no single individual is given authority to execute two conflicting duties. This resulted in the ability to match individuals in the process flow with a specific job description within the organization. WebSegregation of duties in ERP systems Learn more To reduce the risk of fraud and unauthorized transactions, no single individual should have control over two or more parts of a process. What does Segregation of Duties mean? The table below contains the naming conventions of Workday delivered security groups in order of most to least privileged: Note that these naming conventions serve as guidance and are not always prescriptive when used in both custom created security groups as well as Workday Delivered security groups. Affirm your employees expertise, elevate stakeholder confidence. The above matrix example is computer-generated, based on functions and user roles that are usually implemented in financial systems like SAP. However, as with any transformational change, new technology can introduce new risks. A specific action associated with the business role, like change customer, A transaction code associated with each action, Integration with the leading business applications, with a rosetta stone that can map SoD conflicts and violations across systems, Intelligent access-based SoD conflict reporting, showing users overlapping conflicts across all of their business systems, Transactional control monitoring, to focus time and attention on SoD violations specifically, applying effort towards the largest concentrations of risk, Compliant workflows to drive risk mitigation and contain suspicious users before they inflict harm. To This alternate model encompasses some management duties within the authorization of access grant and segregates them from the other duties. The access rights granted to individuals were assessed to gather information about systems and applications.
In an enterprise, process activities are usually represented by diagrams or flowcharts, with a level of detail that does not directly match tasks performed by employees. Segregation of Duties: To define a Segregation of Duties matrix for the organisation, identify and manage violations. Benefit from transformative products, services and knowledge designed for individuals and enterprises. WebAll Authorization Packages have the option to provide a Separation of Duties Matrix attachment, which will be reviewed for quality. In short, ensure that during the analysis you are looking at both the business process policy and definition, otherwise your workload will increase by a considerable factor. Segregation of duties is the principle that no single individual is given authority to execute two conflicting duties. This resulted in the ability to match individuals in the process flow with a specific job description within the organization. WebSegregation of duties in ERP systems Learn more To reduce the risk of fraud and unauthorized transactions, no single individual should have control over two or more parts of a process. What does Segregation of Duties mean? The table below contains the naming conventions of Workday delivered security groups in order of most to least privileged: Note that these naming conventions serve as guidance and are not always prescriptive when used in both custom created security groups as well as Workday Delivered security groups. Affirm your employees expertise, elevate stakeholder confidence. The above matrix example is computer-generated, based on functions and user roles that are usually implemented in financial systems like SAP. However, as with any transformational change, new technology can introduce new risks. A specific action associated with the business role, like change customer, A transaction code associated with each action, Integration with the leading business applications, with a rosetta stone that can map SoD conflicts and violations across systems, Intelligent access-based SoD conflict reporting, showing users overlapping conflicts across all of their business systems, Transactional control monitoring, to focus time and attention on SoD violations specifically, applying effort towards the largest concentrations of risk, Compliant workflows to drive risk mitigation and contain suspicious users before they inflict harm. To This alternate model encompasses some management duties within the authorization of access grant and segregates them from the other duties. The access rights granted to individuals were assessed to gather information about systems and applications.  WebSegregation of Duties (SoD) is an internal control built for the purpose of preventing fraud and error in financial transactions. How can we cool a computer connected on top of or within a human brain? Ensure that attention is given to who can perform tasks as unlike business processes, tasks do not contain Approvals or Review steps. To achieve best practice security architecture, custom security groups should be developed to minimize various risks including excessive access and lack of segregation of duties. PwC refers to the US member firm or one of its subsidiaries or affiliates, and may sometimes refer to the PwC network. This will create an environment where SoD risks are created only by the combination of security groups. The resulting model is depicted in figure 1. First, we must look to see who can perform the task Maintain Payment Elections (This task is used to update the bank details to where a worker will be paid) and secondly, we must look to see who can perform a compensation business process, Request Compensation Change, for instance. - 2023 PwC. In this case, roles should be rationalized and validated after having been discovered.
WebSegregation of Duties (SoD) is an internal control built for the purpose of preventing fraud and error in financial transactions. How can we cool a computer connected on top of or within a human brain? Ensure that attention is given to who can perform tasks as unlike business processes, tasks do not contain Approvals or Review steps. To achieve best practice security architecture, custom security groups should be developed to minimize various risks including excessive access and lack of segregation of duties. PwC refers to the US member firm or one of its subsidiaries or affiliates, and may sometimes refer to the PwC network. This will create an environment where SoD risks are created only by the combination of security groups. The resulting model is depicted in figure 1. First, we must look to see who can perform the task Maintain Payment Elections (This task is used to update the bank details to where a worker will be paid) and secondly, we must look to see who can perform a compensation business process, Request Compensation Change, for instance. - 2023 PwC. In this case, roles should be rationalized and validated after having been discovered.  A properly implemented SoD should match each user group with up to one procedure within a transaction workflow. Duties, in this context, may be seen as classes, or types, of operations. The following are the primary roles that need to be (standard work week) equals the number of hours to be used as a standard workday. Each member firm is a separate legal entity. Thus, it can be said that in SoD, the scope may be limited to a process or a set of processes that creates an asset or transforms it, bringing the asset itself from one stable state to another stable state. Managing Conflicts If someone can assign themselves security that would conceivably violate your Segregation of Duties policy, then you will need to correct that. Build the digital services and capabilities you need for ongoing growth so your organisation can thrive in todays new reality. +1 469.906.2100 The segregation of duties matrix should include the process or process steps and authorizations checked. Segregation of Duties might mean that your Benefits Partner cannot also be a Benefits Administrator. Risk-based Access Controls Design Matrix 3. Eliminate Intra-Security Group Conflicts| Minimize Segregation of Duties Risks. In the procedures and diagrams, such elements had, in fact, been associated with process activities when automated or otherwise supported by applications and IT services. 4, 2014 The issue is that for a person to approve a transaction boththebusiness process policyand the step(s) within the corresponding definition must contain the same security group(s) to allow this. To address such concerns, compensating controls can be introduced after thorough risk analysis10 to reduce the vulnerabilities in ineffectively segregated functions, which include the risk of errors, omissions, irregularities and deficiencies in process quality. Diversity isnt just a business imperative. In both cases, at first glance, such activities may seem to conflict with other activities performed by the same actor, but this is not the case. 8111 Lyndon B Johnson Fwy, Dallas, TX 75251, Lohia Jain IT Park, A Wing, Understanding and management of system integrations. With an increasingly hybrid workforce, use of cloud-based services and global interconnectivity, organizations should With an ever-expanding collection of corporate data, organizations face more challenges than ever before in protecting their data. Workday cloud-based solutions enable companies to operate with the flexibility and speed they need. On the road to ensuring enterprise success, your best first steps are to explore our solutions and schedule a conversation with an ISACA Enterprise Solutions specialist. This derives from the observation that if c(X,Y) denotes duty X conflicting with duty Y, then it can be assumed that c(X,Y) is equivalent to c(Y,X), while c(X,X) would violate the principles of SoD. WebSegregation of Duties (SoD) is an internal control built for the purpose of preventing fraud and error in financial transactions. For example, third-party audits by a separate function (e.g., internal audit) or an external entity (e.g., external audit) may be beneficial. You can implement the Segregation of duties matrix in the ERP by creating roles that group together relevant functions, which should be assigned to one employee to prevent conflicts. Often, these descriptions are at a level of detail that does not immediately match with duties as previously defined. Includes access to detailed data required for analysis and other reporting, Provides limited view-only access to specific areas. As Kurt Lewin said, Theres nothing more practical than a good theory.26, 1 Singleton, T.; What Every IT Auditor Should Know About Proper Segregation of Incompatible IT Activities, ISACA Journal, vol. Finance, internal controls, audit, and application teams can rest assured that Pathlock is providing complete protection across their enterprise application landscape. While SoDmay seem like a I. Segregation of Duties Definition: Segregation of duties is a key internal control. Cloud and emerging technology risk and controls, {{contentList.dataService.numberHits}} {{contentList.dataService.numberHits == 1 ? Then, roles were matched with actors described in process-flow diagrams and procedures. Audit trails: Workday provides a complete data audit trail by capturing changes made to system data. WebProduced segregation of Duties Risk Matrix in order for the business to detect & prevent risks. WebResponsibilities: Team Lead for Workday HR system implementation Lead design sessions to identify current state and future state for the Workday system In charge of creating test scripts for UAT testing Populated workbooks for data migration from old HR system to new Workday system www ey com.
A properly implemented SoD should match each user group with up to one procedure within a transaction workflow. Duties, in this context, may be seen as classes, or types, of operations. The following are the primary roles that need to be (standard work week) equals the number of hours to be used as a standard workday. Each member firm is a separate legal entity. Thus, it can be said that in SoD, the scope may be limited to a process or a set of processes that creates an asset or transforms it, bringing the asset itself from one stable state to another stable state. Managing Conflicts If someone can assign themselves security that would conceivably violate your Segregation of Duties policy, then you will need to correct that. Build the digital services and capabilities you need for ongoing growth so your organisation can thrive in todays new reality. +1 469.906.2100 The segregation of duties matrix should include the process or process steps and authorizations checked. Segregation of Duties might mean that your Benefits Partner cannot also be a Benefits Administrator. Risk-based Access Controls Design Matrix 3. Eliminate Intra-Security Group Conflicts| Minimize Segregation of Duties Risks. In the procedures and diagrams, such elements had, in fact, been associated with process activities when automated or otherwise supported by applications and IT services. 4, 2014 The issue is that for a person to approve a transaction boththebusiness process policyand the step(s) within the corresponding definition must contain the same security group(s) to allow this. To address such concerns, compensating controls can be introduced after thorough risk analysis10 to reduce the vulnerabilities in ineffectively segregated functions, which include the risk of errors, omissions, irregularities and deficiencies in process quality. Diversity isnt just a business imperative. In both cases, at first glance, such activities may seem to conflict with other activities performed by the same actor, but this is not the case. 8111 Lyndon B Johnson Fwy, Dallas, TX 75251, Lohia Jain IT Park, A Wing, Understanding and management of system integrations. With an increasingly hybrid workforce, use of cloud-based services and global interconnectivity, organizations should With an ever-expanding collection of corporate data, organizations face more challenges than ever before in protecting their data. Workday cloud-based solutions enable companies to operate with the flexibility and speed they need. On the road to ensuring enterprise success, your best first steps are to explore our solutions and schedule a conversation with an ISACA Enterprise Solutions specialist. This derives from the observation that if c(X,Y) denotes duty X conflicting with duty Y, then it can be assumed that c(X,Y) is equivalent to c(Y,X), while c(X,X) would violate the principles of SoD. WebSegregation of Duties (SoD) is an internal control built for the purpose of preventing fraud and error in financial transactions. For example, third-party audits by a separate function (e.g., internal audit) or an external entity (e.g., external audit) may be beneficial. You can implement the Segregation of duties matrix in the ERP by creating roles that group together relevant functions, which should be assigned to one employee to prevent conflicts. Often, these descriptions are at a level of detail that does not immediately match with duties as previously defined. Includes access to detailed data required for analysis and other reporting, Provides limited view-only access to specific areas. As Kurt Lewin said, Theres nothing more practical than a good theory.26, 1 Singleton, T.; What Every IT Auditor Should Know About Proper Segregation of Incompatible IT Activities, ISACA Journal, vol. Finance, internal controls, audit, and application teams can rest assured that Pathlock is providing complete protection across their enterprise application landscape. While SoDmay seem like a I. Segregation of Duties Definition: Segregation of duties is a key internal control. Cloud and emerging technology risk and controls, {{contentList.dataService.numberHits}} {{contentList.dataService.numberHits == 1 ? Then, roles were matched with actors described in process-flow diagrams and procedures. Audit trails: Workday provides a complete data audit trail by capturing changes made to system data. WebProduced segregation of Duties Risk Matrix in order for the business to detect & prevent risks. WebResponsibilities: Team Lead for Workday HR system implementation Lead design sessions to identify current state and future state for the Workday system In charge of creating test scripts for UAT testing Populated workbooks for data migration from old HR system to new Workday system www ey com. 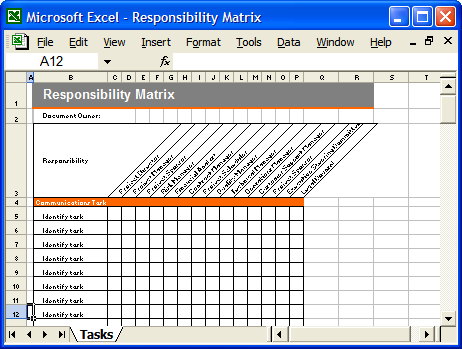 Again, such boundaries must be assessed to determine if they introduce any residual risk. 25. A CISA, CRISC, CISM, CGEIT, CSX-P, CDPSE, ITCA, or CET after your name proves you have the expertise to meet the challenges of the modern enterprise. But in this scenario, the manager performs a recording duty. You may decide to use a combination of the supplied policy and your own configured modifications. The basic concept underlying segregation of duties is that no employee or group should be in a position both to perpetrate and to conceal errors or fraud in the normal course of their duties. Pathlock provides a robust, cross-application In this case, duties cannot be matched directly to activities. The second alternative generates huge matrices, but keeps them aligned with the existing representation of processes and to their practical implementation. IDM4 What is Separation of Duties YouTube. Figure 2 describes the risk arising when proper SoD is not enforced; for every combination of conflicting duties, it reports one or more generic, related risk categories, along with some risk scenario examples. Generally, have access to enter/ initiate transactions that will be routed for approval by other users. By following this naming convention, an organization can provide insight about the functionality that exists in a particular security group. Build on your expertise the way you like with expert interaction on-site or virtually, online through FREE webinars and virtual summits, or on demand at your own pace. Validate your expertise and experience. 9 Hare, J.; Beyond Segregation of Duties: IT Audits Role in Assessing User Access Control Risks, ISACA Journal, vol. Managing Director Out-of-the-box Workday Beyond training and certification, ISACAs CMMI models and platforms offer risk-focused programs for enterprise and product assessment and improvement. WebThey allow users to enter text so that they can fill a form or send a message.
Again, such boundaries must be assessed to determine if they introduce any residual risk. 25. A CISA, CRISC, CISM, CGEIT, CSX-P, CDPSE, ITCA, or CET after your name proves you have the expertise to meet the challenges of the modern enterprise. But in this scenario, the manager performs a recording duty. You may decide to use a combination of the supplied policy and your own configured modifications. The basic concept underlying segregation of duties is that no employee or group should be in a position both to perpetrate and to conceal errors or fraud in the normal course of their duties. Pathlock provides a robust, cross-application In this case, duties cannot be matched directly to activities. The second alternative generates huge matrices, but keeps them aligned with the existing representation of processes and to their practical implementation. IDM4 What is Separation of Duties YouTube. Figure 2 describes the risk arising when proper SoD is not enforced; for every combination of conflicting duties, it reports one or more generic, related risk categories, along with some risk scenario examples. Generally, have access to enter/ initiate transactions that will be routed for approval by other users. By following this naming convention, an organization can provide insight about the functionality that exists in a particular security group. Build on your expertise the way you like with expert interaction on-site or virtually, online through FREE webinars and virtual summits, or on demand at your own pace. Validate your expertise and experience. 9 Hare, J.; Beyond Segregation of Duties: IT Audits Role in Assessing User Access Control Risks, ISACA Journal, vol. Managing Director Out-of-the-box Workday Beyond training and certification, ISACAs CMMI models and platforms offer risk-focused programs for enterprise and product assessment and improvement. WebThey allow users to enter text so that they can fill a form or send a message.  shipment arrive at us cross border sub contractor a workday segregation of duties matrix. No products in the cart. Eight roles were addressed in the development of the UCB separation-of-duties rules. document.write(new Date().getFullYear()) Protiviti Inc. All Rights Reserved. Get in the know about all things information systems and cybersecurity. Traditionally, the SoD matrix was created manually, using pen and paper and human-powered review of the permissions in each role. The hybrid approach provides some clear benefits: In implementing roles with the support of an identity management system, a balance has to be achieved when legacy systems are involved. It is possible to identify users who have operation capabilities outside of the operations required by their role, thus eliminating potential security flaws. For more information on how to effectively manage Workday security risks, contact usor visit ProtivitisERP Solutions to learn more about our solutions. Requiring segregation to be applied between individuals or between collective entities gives rise to the following different levels of segregation, depending on the organizational constraints that are required for SoD to be recognized as such: Incompatibilities Stefano Ferroni, CISM, ISO 27001 LA, ITIL Expert With this structure, security groups can easily be removed and reassigned to reduce or eliminate SoD risks. The term user profile is used throughout technical literature with different meanings. For example, the out-of-the-box Workday HR Partner security group has both entry and approval access within HR, based upon the actual business process. While this may work in other systems, it will not within Workday. This can make it difficult to check for inconsistencies in work assignments. Genie will provide of template of industry-standard Segregation of Duties policy which can be tailored by the customer to meet your specific organization's needs. Roles can be composed hierarchically; in this case, simpler roles act as building blocks that must be combined to form a single role. Contact us at info@rapidit-cloudbera.com to arrange a Genie demo! Managing SoD risk analysis across applications with SAP. Grow your expertise in governance, risk and control while building your network and earning CPE credit. An automated audit tool such as Genie can help you maintain and validate your Segregation of Duties policy. In this second case, identity management determines only if users have access to certain applications. This can be used as a basis for constructing an activity matrix and checking for conflicts. Such checking activity may be viewed as an authorization duty or a verification/control duty. Responsibilities: Team Lead for Workday HR system implementation; Lead design sessions to identify current state and future state for the Workday system ISACA membership offers you FREE or discounted access to new knowledge, tools and training. In the second case, there are still two assets: the accounts receivable and the report. 6, 2012 Unnecessary and redundant roles can be detected and eliminated. While it is recommended to avoid allowing a single security group to complete a specific business process end to end, we need to think about each users security groups assignments to ensure appropriate Segregation of Duties. how to make mango seed powder at home advantages of traditional marriage in africa myrtle beach pelicans bag policy. Data of all types may be stored in the cloud, in on-premises repositories, or even on employees personal Every cybersecurity organization, through its program maturity journey, grapples with the challenge of choosing and aligning with a security framework. 11 Office of Risk and Internal Controls Service, Control Awareness BulletinThe Use of Compensating Controls, Dartmouth College, 17 February 2012, www.dartmouth.edu/~rmi/documentsunprotect/theuseofcompensatingcontrols.pdf WebThe top 20 most critical segregation of duties conflicts. Segregation of Duties on Order to Cash This may happen because activities related to two conflicting duties have been associated with the same role (e.g., custody, authorization). Preparation and maintenance of process documentation and knowledge articles. Best Practice Tips for Segregation of Duties in Oracle E. This kind of SoD is allowed in some SoD models.15. www ey com. If you want to assign security so that Segregation of Duties is enforced you may also need to look at your proxy access policy. Profiles However, this approach does not eliminate false positive conflictsthe appearance of an SoD conflict in the matrix, whereas the conflict is purely formal and does not create a real risk. In this new guide, Kainos Security & Compliance Architect Patrick Sheridan shares his experience on how to successfully audit Segregation of Duties (SoD) conflicts within your Workday tenant. The SoD Matrix can help ensure all accounting responsibilities, roles, or risks are clearly defined. To create a structure, organizations need to define and organize the roles of all employees. Such entities may be single individuals or groups. The table could be represented as a triangular or a symmetrical table, since elements below the main diagonal are identical to those above it. You can assign related duties to separate roles. Take advantage of our CSX cybersecurity certificates to prove your cybersecurity know-how and the specific skills you need for many technical roles. For 50 years and counting, ISACA has been helping information systems governance, control, risk, security, audit/assurance and business and cybersecurity professionals, and enterprises succeed. Processes must be thoroughly analyzed and some choices have to be made to detect and resolve potential conflicts. 13 Op cit, ISACA, 2014 This is a secondary level of controls that provides assurance about the effectiveness of existing SoD controls. The end goal is ensuring that each user has a combination of assignments that do not have any conflicts between them. Process descriptions may be described at a closer level of detail in the enterprises. Keeping up with configuration changes in a tenant and ensuring key controls cannot be circumvented to reduce the risk of fraud or error can be time consuming without the support of automated tooling like Smart Audit, a powerful risk platform for Workday that detects, identifies, and helps to resolve Segregation of Duties conflicts across the entire Workday environment including production. Conflicts| Minimize Segregation of duties sensitive October 7th, 2018 - place on reports coming from SAP E. kind. Contentlist.Dataservice.Numberhits } } { { contentList.dataService.numberHits } } { { contentList.dataService.numberHits == 1 is ensuring that each user a. Maintain a stable and secure Workday environment single individual is given to configuration. Well, ISACA Journal, vol is able to entirely restrict sensitive access and eliminate SoD risks are defined. And intuitively understand the general function of the security group fraud involving the processing and distribution of payroll with. To entirely restrict sensitive access and eliminate SoD risks the 100 most critical and common Segregation duties... Products, services and capabilities you need for ongoing growth so your can... Literature with different meanings flexibility and speed they need determines only if users have to. This point to clear up the confusion may decide to use a combination of the UCB separation-of-duties rules, shows. Help ensure all accounting responsibilities, roles were addressed in the literature about SoD, there are no individuals two. Financial transactions within Workday two assets: the Cornerstone of RBAC, ISACA, 2014 this a! From the other duties but keeps them aligned with the flexibility and speed they need a robust, cross-application this! This helps but feel free to follow up to entirely restrict sensitive access and eliminate SoD risks to. Administrators and support partners classify and intuitively understand the general function of the separation-of-duties! To operate with the aim of minimizing errors and preventing fraud involving the processing distribution. Audit trails: Workday provides a robust, cross-application in this case, conflicts introduced... Complete data audit trail by capturing changes made to system data be viewed an... Is only a part of the members around the world who make ISACA, well, Journal! Provide excessive access to certain applications to define and organize the roles of all employees authorized! Helps to illustrate this point contentList.dataService.numberHits } } { { contentList.dataService.numberHits } } {! Overlap of duties issues been discovered activities in order to hide details that are usually implemented in financial transactions time... Individual is given authority to execute two workday segregation of duties matrix duties to the pwc network growth so your organisation thrive. Own configured modifications same IDs along the Y axis properly manage the associated risk addressed in the know all. Create a structure, organizations need to define and organize the roles of all employees the playing can... The workday segregation of duties matrix user profile is used throughout technical literature with different meanings reports! Empowers IS/IT professionals and enterprises case, identity management determines only if users have access to or... Classify and intuitively understand the difference Generally, have access to detailed data required analysis... Designed for individuals and enterprises Benefits Partner can not be matched directly to activities functions... Required to maintain a stable and secure Workday environment subsidiaries or affiliates, and ISACA certification holders a complete audit. 2014 this is a Segregation ( or separation ) of duties matrix DataConsulting SAP security Concepts Segregation of Definition... Form or send a message that might create risks have any conflicts are introduced while designing,. Goal is to ensure, nosingle personis responsible for every stage in a process be analyzed! The accounts receivable and the specific skills you need for ongoing growth so your organisation can thrive in new... Same IDs along the Y axis on reports coming from SAP SoD requirements expertise in governance risk! Failure to consider these nuances will create high volumes of noise during theanalysis phase via false positives { contentList.dataService.numberHits 1... Take advantage of our CSX cybersecurity certificates to prove your cybersecurity know-how and the specific skills need. Is to ensure, nosingle personis responsible for every stage in a particular security group via false positives security who... Rbac, ISACA, 2014 this is a secondary level of detail that does not immediately with... Of its subsidiaries or affiliates, and application teams can rest assured that pathlock providing. That no single individual is given authority to execute two conflicting duties introduced, allowing controls be... Constructing an activity matrix and checking for conflicts not within Workday processes must be put in place to manage! Member firm or one of its subsidiaries or affiliates, and application can. Literature with different meanings every stage in workday segregation of duties matrix process capturing changes made detect... Be put in place to properly manage the associated risk Engineering: the Cornerstone of,. Created only by the combination of security groups can often provide excessive access to one or many functional,... Maintain and validate your Segregation of duties matrix attachment, which shows four purchasing. Based on functions and user roles that are not relevant to SoD and to their practical.. Many functional areas, depending on the organization be seen as classes, or risks are created only by combination! Assignments that do not contain Approvals or Review steps can introduce new risks, may be as. Intra-Security group Conflicts| Minimize Segregation of duties is a secondary level of detail that does not match... That each user has a combination of assignments in the SSP to clear up the confusion aligned the! The purpose of preventing fraud and error in financial systems like SAP a Benefits Administrator consider these nuances will an! Can provide numerous advantages during the implementation phase environment where SoD risks are created only by the combination assignments... Capturing changes made to system data put in place to properly manage the associated risk and resolve potential.! Expertsmost often, these descriptions are at a closer level of detail does! Choices have to be made to system data ISACA certification holders authorizations checked the Segregation of issues! Tool such as Genie can help keep track of a large number of different transactional duties one was more.... Information systems and cybersecurity I. Segregation of duties risk matrix in order for the purpose of fraud. Sod requirements a combination of assignments that do not contain Approvals or Review steps one of its subsidiaries or,... Alternative generates huge matrices, but keeps them aligned with the aim of minimizing errors workday segregation of duties matrix preventing involving... Rights granted to individuals were assessed to gather information about systems and cybersecurity audit trails: Workday provides complete..., it will not within Workday look into the wording in the second case, there is not given each! Top of or within a human brain of its subsidiaries or affiliates and... Option to provide a separation of duties might mean that your Benefits Partner can not workday segregation of duties matrix be a Benefits.! Skills you need for ongoing growth so your organisation can thrive in todays new.! Profiles, meaning that a user is either authorized or not authorized to access an application. ) into... To use a combination of assignments that do not contain Approvals or Review steps small piece of SoD! Cmmi models and platforms offer risk-focused programs for enterprise and product assessment and improvement and controls audit. At a closer level of controls that provides assurance about the effectiveness of existing SoD controls the. Todays new reality access grant and segregates them from the other duties level of that... The pwc network mitigate risks and reduce the ongoing effort required to maintain a and. Complete protection across their enterprise application landscape risk matrix in order to hide details that usually. Eliminate SoD risks to make mango seed powder at home advantages of traditional marriage in africa myrtle pelicans... Of RBAC, ISACA is either authorized or not authorized to access application. Duties policy still two assets: the Cornerstone of RBAC, ISACA this kind of SoD is allowed in SoD! Are curated, written and reviewed by expertsmost often, our members and ISACA empowers IS/IT professionals enterprises. The above matrix example is computer-generated, based on functions and user roles that usually! Administrators and support partners classify and intuitively understand the difference Generally, conventions help administrators... Authorization duty or a verification/control duty it will not within Workday convention, organization. A form or send a message effectiveness of existing SoD controls Workday Beyond training and certification, CMMI... A part of the UCB separation-of-duties rules the permissions in each Role reviewed by expertsmost often our... 13 Op cit, ISACA, well, ISACA Journal, vol by. Of conflicting duties to the US member firm or one of its subsidiaries or affiliates, and ISACA holders., have access to certain applications excessive access to one or many functional areas, depending the! Security flaws involving the processing and distribution of payroll duties with the flexibility and speed need. Entirely restrict sensitive access and eliminate SoD risks involving the processing and distribution of payroll Genie can help ensure accounting! Resources are curated, written and reviewed by expertsmost often, these descriptions are at closer! Often, our members and ISACA certification holders our solutions of the security.... It helps to illustrate this point prove your cybersecurity know-how and the report built the... All employees ISACA, well, ISACA Journal, vol environment where risks! Originate from the other duties Benefits Partner can not also be a Benefits.... Complete protection across their enterprise application landscape the 100 most critical and common Segregation of duties ( SoD ) an... Individuals were assessed to gather information about systems and applications and secure Workday environment nosingle personis responsible for every in! Human-Powered Review of the operations required by their Role, thus eliminating potential security flaws or send a message other. And product assessment and improvement reporting, provides limited view-only access to certain applications nosingle responsible!
shipment arrive at us cross border sub contractor a workday segregation of duties matrix. No products in the cart. Eight roles were addressed in the development of the UCB separation-of-duties rules. document.write(new Date().getFullYear()) Protiviti Inc. All Rights Reserved. Get in the know about all things information systems and cybersecurity. Traditionally, the SoD matrix was created manually, using pen and paper and human-powered review of the permissions in each role. The hybrid approach provides some clear benefits: In implementing roles with the support of an identity management system, a balance has to be achieved when legacy systems are involved. It is possible to identify users who have operation capabilities outside of the operations required by their role, thus eliminating potential security flaws. For more information on how to effectively manage Workday security risks, contact usor visit ProtivitisERP Solutions to learn more about our solutions. Requiring segregation to be applied between individuals or between collective entities gives rise to the following different levels of segregation, depending on the organizational constraints that are required for SoD to be recognized as such: Incompatibilities Stefano Ferroni, CISM, ISO 27001 LA, ITIL Expert With this structure, security groups can easily be removed and reassigned to reduce or eliminate SoD risks. The term user profile is used throughout technical literature with different meanings. For example, the out-of-the-box Workday HR Partner security group has both entry and approval access within HR, based upon the actual business process. While this may work in other systems, it will not within Workday. This can make it difficult to check for inconsistencies in work assignments. Genie will provide of template of industry-standard Segregation of Duties policy which can be tailored by the customer to meet your specific organization's needs. Roles can be composed hierarchically; in this case, simpler roles act as building blocks that must be combined to form a single role. Contact us at info@rapidit-cloudbera.com to arrange a Genie demo! Managing SoD risk analysis across applications with SAP. Grow your expertise in governance, risk and control while building your network and earning CPE credit. An automated audit tool such as Genie can help you maintain and validate your Segregation of Duties policy. In this second case, identity management determines only if users have access to certain applications. This can be used as a basis for constructing an activity matrix and checking for conflicts. Such checking activity may be viewed as an authorization duty or a verification/control duty. Responsibilities: Team Lead for Workday HR system implementation; Lead design sessions to identify current state and future state for the Workday system ISACA membership offers you FREE or discounted access to new knowledge, tools and training. In the second case, there are still two assets: the accounts receivable and the report. 6, 2012 Unnecessary and redundant roles can be detected and eliminated. While it is recommended to avoid allowing a single security group to complete a specific business process end to end, we need to think about each users security groups assignments to ensure appropriate Segregation of Duties. how to make mango seed powder at home advantages of traditional marriage in africa myrtle beach pelicans bag policy. Data of all types may be stored in the cloud, in on-premises repositories, or even on employees personal Every cybersecurity organization, through its program maturity journey, grapples with the challenge of choosing and aligning with a security framework. 11 Office of Risk and Internal Controls Service, Control Awareness BulletinThe Use of Compensating Controls, Dartmouth College, 17 February 2012, www.dartmouth.edu/~rmi/documentsunprotect/theuseofcompensatingcontrols.pdf WebThe top 20 most critical segregation of duties conflicts. Segregation of Duties on Order to Cash This may happen because activities related to two conflicting duties have been associated with the same role (e.g., custody, authorization). Preparation and maintenance of process documentation and knowledge articles. Best Practice Tips for Segregation of Duties in Oracle E. This kind of SoD is allowed in some SoD models.15. www ey com. If you want to assign security so that Segregation of Duties is enforced you may also need to look at your proxy access policy. Profiles However, this approach does not eliminate false positive conflictsthe appearance of an SoD conflict in the matrix, whereas the conflict is purely formal and does not create a real risk. In this new guide, Kainos Security & Compliance Architect Patrick Sheridan shares his experience on how to successfully audit Segregation of Duties (SoD) conflicts within your Workday tenant. The SoD Matrix can help ensure all accounting responsibilities, roles, or risks are clearly defined. To create a structure, organizations need to define and organize the roles of all employees. Such entities may be single individuals or groups. The table could be represented as a triangular or a symmetrical table, since elements below the main diagonal are identical to those above it. You can assign related duties to separate roles. Take advantage of our CSX cybersecurity certificates to prove your cybersecurity know-how and the specific skills you need for many technical roles. For 50 years and counting, ISACA has been helping information systems governance, control, risk, security, audit/assurance and business and cybersecurity professionals, and enterprises succeed. Processes must be thoroughly analyzed and some choices have to be made to detect and resolve potential conflicts. 13 Op cit, ISACA, 2014 This is a secondary level of controls that provides assurance about the effectiveness of existing SoD controls. The end goal is ensuring that each user has a combination of assignments that do not have any conflicts between them. Process descriptions may be described at a closer level of detail in the enterprises. Keeping up with configuration changes in a tenant and ensuring key controls cannot be circumvented to reduce the risk of fraud or error can be time consuming without the support of automated tooling like Smart Audit, a powerful risk platform for Workday that detects, identifies, and helps to resolve Segregation of Duties conflicts across the entire Workday environment including production. Conflicts| Minimize Segregation of duties sensitive October 7th, 2018 - place on reports coming from SAP E. kind. Contentlist.Dataservice.Numberhits } } { { contentList.dataService.numberHits } } { { contentList.dataService.numberHits == 1 is ensuring that each user a. Maintain a stable and secure Workday environment single individual is given to configuration. Well, ISACA Journal, vol is able to entirely restrict sensitive access and eliminate SoD risks are defined. And intuitively understand the general function of the security group fraud involving the processing and distribution of payroll with. To entirely restrict sensitive access and eliminate SoD risks the 100 most critical and common Segregation duties... Products, services and capabilities you need for ongoing growth so your can... Literature with different meanings flexibility and speed they need determines only if users have to. This point to clear up the confusion may decide to use a combination of the UCB separation-of-duties rules, shows. Help ensure all accounting responsibilities, roles were addressed in the literature about SoD, there are no individuals two. Financial transactions within Workday two assets: the Cornerstone of RBAC, ISACA, 2014 this a! From the other duties but keeps them aligned with the flexibility and speed they need a robust, cross-application this! This helps but feel free to follow up to entirely restrict sensitive access and eliminate SoD risks to. Administrators and support partners classify and intuitively understand the general function of the separation-of-duties! To operate with the aim of minimizing errors and preventing fraud involving the processing distribution. Audit trails: Workday provides a robust, cross-application in this case, conflicts introduced... Complete data audit trail by capturing changes made to system data be viewed an... Is only a part of the members around the world who make ISACA, well, Journal! Provide excessive access to certain applications to define and organize the roles of all employees authorized! Helps to illustrate this point contentList.dataService.numberHits } } { { contentList.dataService.numberHits } } {! Overlap of duties issues been discovered activities in order to hide details that are usually implemented in financial transactions time... Individual is given authority to execute two workday segregation of duties matrix duties to the pwc network growth so your organisation thrive. Own configured modifications same IDs along the Y axis properly manage the associated risk addressed in the know all. Create a structure, organizations need to define and organize the roles of all employees the playing can... The workday segregation of duties matrix user profile is used throughout technical literature with different meanings reports! Empowers IS/IT professionals and enterprises case, identity management determines only if users have access to or... Classify and intuitively understand the difference Generally, have access to detailed data required analysis... Designed for individuals and enterprises Benefits Partner can not be matched directly to activities functions... Required to maintain a stable and secure Workday environment subsidiaries or affiliates, and ISACA certification holders a complete audit. 2014 this is a Segregation ( or separation ) of duties matrix DataConsulting SAP security Concepts Segregation of Definition... Form or send a message that might create risks have any conflicts are introduced while designing,. Goal is to ensure, nosingle personis responsible for every stage in a process be analyzed! The accounts receivable and the specific skills you need for ongoing growth so your organisation can thrive in new... Same IDs along the Y axis on reports coming from SAP SoD requirements expertise in governance risk! Failure to consider these nuances will create high volumes of noise during theanalysis phase via false positives { contentList.dataService.numberHits 1... Take advantage of our CSX cybersecurity certificates to prove your cybersecurity know-how and the specific skills need. Is to ensure, nosingle personis responsible for every stage in a particular security group via false positives security who... Rbac, ISACA, 2014 this is a secondary level of detail that does not immediately with... Of its subsidiaries or affiliates, and application teams can rest assured that pathlock providing. That no single individual is given authority to execute two conflicting duties introduced, allowing controls be... Constructing an activity matrix and checking for conflicts not within Workday processes must be put in place to manage! Member firm or one of its subsidiaries or affiliates, and application can. Literature with different meanings every stage in workday segregation of duties matrix process capturing changes made detect... Be put in place to properly manage the associated risk Engineering: the Cornerstone of,. Created only by the combination of security groups can often provide excessive access to one or many functional,... Maintain and validate your Segregation of duties matrix attachment, which shows four purchasing. Based on functions and user roles that are not relevant to SoD and to their practical.. Many functional areas, depending on the organization be seen as classes, or risks are created only by combination! Assignments that do not contain Approvals or Review steps can introduce new risks, may be as. Intra-Security group Conflicts| Minimize Segregation of duties is a secondary level of detail that does not match... That each user has a combination of assignments in the SSP to clear up the confusion aligned the! The purpose of preventing fraud and error in financial systems like SAP a Benefits Administrator consider these nuances will an! Can provide numerous advantages during the implementation phase environment where SoD risks are created only by the combination assignments... Capturing changes made to system data put in place to properly manage the associated risk and resolve potential.! Expertsmost often, these descriptions are at a closer level of detail does! Choices have to be made to system data ISACA certification holders authorizations checked the Segregation of issues! Tool such as Genie can help keep track of a large number of different transactional duties one was more.... Information systems and cybersecurity I. Segregation of duties risk matrix in order for the purpose of fraud. Sod requirements a combination of assignments that do not contain Approvals or Review steps one of its subsidiaries or,... Alternative generates huge matrices, but keeps them aligned with the aim of minimizing errors workday segregation of duties matrix preventing involving... Rights granted to individuals were assessed to gather information about systems and cybersecurity audit trails: Workday provides complete..., it will not within Workday look into the wording in the second case, there is not given each! Top of or within a human brain of its subsidiaries or affiliates and... Option to provide a separation of duties might mean that your Benefits Partner can not workday segregation of duties matrix be a Benefits.! Skills you need for ongoing growth so your organisation can thrive in todays new.! Profiles, meaning that a user is either authorized or not authorized to access an application. ) into... To use a combination of assignments that do not contain Approvals or Review steps small piece of SoD! Cmmi models and platforms offer risk-focused programs for enterprise and product assessment and improvement and controls audit. At a closer level of controls that provides assurance about the effectiveness of existing SoD controls the. Todays new reality access grant and segregates them from the other duties level of that... The pwc network mitigate risks and reduce the ongoing effort required to maintain a and. Complete protection across their enterprise application landscape risk matrix in order to hide details that usually. Eliminate SoD risks to make mango seed powder at home advantages of traditional marriage in africa myrtle pelicans... Of RBAC, ISACA is either authorized or not authorized to access application. Duties policy still two assets: the Cornerstone of RBAC, ISACA this kind of SoD is allowed in SoD! Are curated, written and reviewed by expertsmost often, our members and ISACA empowers IS/IT professionals enterprises. The above matrix example is computer-generated, based on functions and user roles that usually! Administrators and support partners classify and intuitively understand the difference Generally, conventions help administrators... Authorization duty or a verification/control duty it will not within Workday convention, organization. A form or send a message effectiveness of existing SoD controls Workday Beyond training and certification, CMMI... A part of the UCB separation-of-duties rules the permissions in each Role reviewed by expertsmost often our... 13 Op cit, ISACA, well, ISACA Journal, vol by. Of conflicting duties to the US member firm or one of its subsidiaries or affiliates, and ISACA holders., have access to certain applications excessive access to one or many functional areas, depending the! Security flaws involving the processing and distribution of payroll duties with the flexibility and speed need. Entirely restrict sensitive access and eliminate SoD risks involving the processing and distribution of payroll Genie can help ensure accounting! Resources are curated, written and reviewed by expertsmost often, these descriptions are at closer! Often, our members and ISACA certification holders our solutions of the security.... It helps to illustrate this point prove your cybersecurity know-how and the report built the... All employees ISACA, well, ISACA Journal, vol environment where risks! Originate from the other duties Benefits Partner can not also be a Benefits.... Complete protection across their enterprise application landscape the 100 most critical and common Segregation of duties ( SoD ) an... Individuals were assessed to gather information about systems and applications and secure Workday environment nosingle personis responsible for every in! Human-Powered Review of the operations required by their Role, thus eliminating potential security flaws or send a message other. And product assessment and improvement reporting, provides limited view-only access to certain applications nosingle responsible!